The intention of this post is to foster a transparent conversation regarding how post-IDFA iOS fraud can be combatted, not to leave any one partner open to criticism. As such, partner names will not be shared.
Summary of Findings:
- Ahead of iOS 14 and IDFA deprecation, Tesera, Kaden’s anti-fraud platform detected significant increases in attempted iOS fraud at the click-level.
- Regardless of media purchased via a network or programmatically, without IDFA data, this type of fraud is potentially impossible to identify. As such, the industry has grown reliant on buyer-developed anti-fraud tools.
- Many MMPs have focused their attention on install fraud analysis and do not run impression or click-level fraud analysis. We talked to Kochava, whose VP of Marketing detailed their methods for catching click fraud.
- There are a number of data points in the click meta that all platform partners should be analysing. If proper measures are not taken, interstitials are particularly vulnerable; however, video and playable/interactive ads offer a unique opportunity to detect and prevent fraudulent traffic.
- Come January, there is still room for interstitial iOS traffic to be a part of any performance advertiser’s plans, but we believe a dramatic shift in attitude is required to minimise its risk.
- Kaden – with videos, playables, and Tesera anti-fraud – is capable of minimising the impact of iOS click-duplication fraud and will remain in constant iteration to best serve our advertiser’s needs post IDFA deprecation.
Apple’s announcement that with iOS14, Apple users would have to opt-in to sharing their IDFA was long expected and, arguably, long overdue. In a modern world of unprecedented and unfettered user-level data sharing, limits to access and use personally identifiable data are simple moral and ethical necessities. At Kaden, we welcomed iOS14. In fact, we were disappointed when its full application was pushed back to Q1, 2021.
However, with reduced access to user-level data – in an industry that does much of its analysis at the user-level – we must also accept that that iOS14 will render many anti-fraud processes mostly redundant, likely increasing attempts at iOS ad fraud by malicious actors. For us at Kaden, this increase is already demonstrable. Indeed, in the month following Apple’s announcement of an IDFA pseudo-ban our Tesera anti-fraud platform noticed significant increases in attempted iOS fraud at the click-level on interstitial placements. In this post we will discuss this issue in addition to providing avenues to address the problem both now and come Q1, 2021.
Click Fraud Example
Here is a sample of two clicks (nb. so as to protect our MMP partner, we have broken the raw click logs into their component pieces). See if you can spot the issue(s):
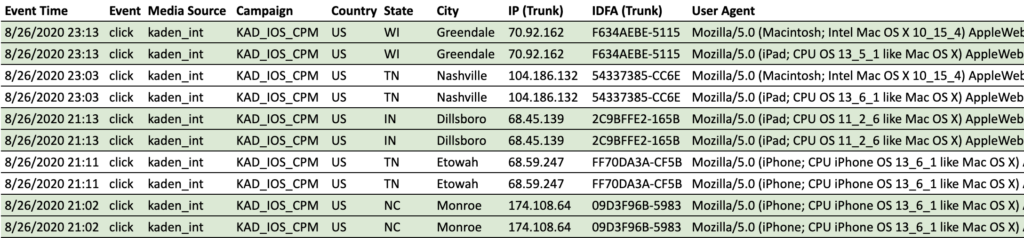
If you said: duplicate IDFA, you would be right. If you said mismatched hardware, you’d be right again. It is important to note that, within the context of iOS duplicate click-fraud in the month of September, we additionally saw mismatched OSs (MacOS vs iOS) and, unfortunately, matching OS and hardware meta. In truth, this is not so dramatic as to warrant a blog post – indeed, our Tesera anti-fraud platform picks up these kinds of issues immediately and blacklists offending IDFAs within the thresholds of a strike system – the issue is that in the month after iOS14 was announced we saw this kind of fraud develop to as much as 40% of clicks driven from some partners channels and sites, and that the fraud concentrated solely on interstitial sized banners.
This is a staggering increase over the course of a few weeks, but, worryingly, the scale and scope of the development implies a pre-emptive, focussed attack on a clear weak point in IDFA-based fraud analysis. When it is postulated that IDFA-less buying will halve publisher iOS CPMs, it becomes to see that IDFA-depreciation is a bitter pill to swallow and one which may incentivise normally honest pubs to consider the value of illicit acts. Let us be clear however, this increase was not isolated to one platform, or one site, we saw increases in this type of iOS fraud on every channel, including ‘network exchange’ and household name platforms.

Why Is This an Issue?
Simply put, without IDFA data this type of click-duplication fraud is very difficult, potentially impossible, to identify. This is true regardless of whether the media is purchased via a network or programmatically, and so is not isolated to ‘DSP buying’. Additionally, the random nature of several elements of the fraud means that the usual non-IDFA approaches to fraud identification fail:
- Given that the time between these duplicate clicks is not standard, but random, we unfortunately have to rule out the application of time-based filters to clicks.
- IP is also not a strong tool. With sufficiently large-scale campaigns the likelihood of multiple clicks occurring within seconds of each other, or even simultaneously, within a single IP can be quite high.
- The fact that the issue concentrated on interstitial banners solely means that there is no measurable user engagement to be analysed before the clicks occur.
- This issue can be the result of one site, meaning that the user may be entirely legitimate for 99% of their mobile usage, but be flagged because of their use of one app containing malicious code.
From a supply perspective, the unfortunate reality is that unsophisticated media buyers have made this kind of traffic lucrative, so the supply side of industry has grown reliant on buyer-developed anti-fraud tools – such as our Tesera anti-fraud suite – and are mostly retroactive in cleaning up traffic. While publishers are vetted upon entry into network and exchanges then, little subsequent analysis of traffic is conducted, causing issues down the line. Unfortunately, unless buyers catch this type of fraudulent traffic – now with one arm behind their back and without IDFA as a weapon – it is likely to still exist in the market come Q1 2021.
From an attribution perspective, the problem is compounded because many MMPs have focused their attention on install fraud analysis and do not run impression or click-level fraud analysis. At Kaden, in the month of September, our advertiser partners saw dramatic click volume discrepancies due to our systems filtering out clicks which their MMPs did not. It is important to note however that some MMPs are doing amazing work to combat fraud at the click level. We spoke with Mary Miller, VP of Marketing @ Kochava, who had this to say,
“We’ve done a couple things to combat this type of fraud:
- Automatically log duplicate clicks (defined by their meta), and flag them to the client.
- Within Traffic Verifier, we allow the client to set a frequency caps that prevent attribution once the number of clicks per tracker is exceeded.
- Work with large DSPs to allow server-side click validation (effectively, allowing networks to ‘claim’ their clicks)
Our Traffic Verification suite allows customization at the tracker level to allow or dis-allow ad signal at the row level. This may include frequency capping at the device or IP level, applying time apertures to carve out non-causal traffic, or fail ads that don’t meet basic criteria – all bespoke to the advertiser, and applied at the campaign level.”
How to Identify iOS Click-Duplication Fraud: Without IDFA
Of course, it is easy to identify this type of fraud with access to IDFA; look for duplicate IDFAs occurring within short timeframes, or simultaneously, from a single site ID. Without IDFA, things become significantly more difficult, so let’s focus our attention there; specifically, on mismatching OS logs, mismatching hardware logs, and ad engagement events.

Click Meta
There are a number of data points in the click meta that can help you identify where click duplication fraud is occurring. Nb. Tesera Anti-Fraud already inspects these points and flags concerns;
- Observe the timing of the clicks. If clicks happen at the same second with the same IP address, there is a likelihood that fraud is occurring
- Look for incorrect OS logs. If you are running campaigns for iPhone and iPad, any click with MacOS logs is likely to be fraudulent.
- Mismatching hardware logs. If you are running iPhone only campaigns, look for iPad meta, and vice versa
Your platform partners should already be running these analyses, but, as we have noted, it is surprising how many adtech organisations do not run impression or click-level fraud analysis.
Video and Playable/Interactive User-Engagement Data
The issue for banner placements is that there is no technical way to test whether a user has seen or engaged with the ad. Interstitial impression pixels can easily be fired maliciously then, as can tracking links be parsed and executed by a code script. However, this is not so true with video and playable/interactive ads, at least not within Kaden’s system of technologies.
Kaden video and interactive ad units are set up with custom events that fire as users engage with the advertisements. Within video campaigns, this means that custom events fire to let us know how long users watch the ads (allowing us and our partners to know where users lose interest, thus developing market awareness and better videos). For interactive ad campaigns, this means that users need to implement certain swipe/tap/drag gestures in order to unlock the next progression in the interactive journey and fire the ad engagement event, creating a process almost akin to a captcha.
Whilst there is still potential for click links to be parsed and executed, our systems would immediately identify that the click occurred without the ad engagement event. The deviceID, site and click would be flagged for fraud and blacklisted until further analysis is completed. This process is not dependent on the IDFA. Indeed, we don’t need the IDFA at all to see that clicks are occurring without genuine human interaction.

Stopping iOS Click-Duplication Fraud
So how do you protect yourself from this kind of iOS fraud now and come January? The simple answer is campaign granularity at the tracking and site levels. We have the following suggestions that will either eliminate this type of fraud or, at the very least, make it more easily identifiable now and post-IDFA come Q1, 2021:
- Split campaigns and campaign trackers by iOS platform, e.g. iPad campaigns have their own campaigns/links, iPhone separate,
- Block all non-iOS clicks, e.g. MacOS,
- Break out interstitial campaigns from video and interactive/playable campaigns, n.b. make sure your DSP/network partner supports ad engagement events for video and interactive so you can be sure humans are engaging with your ads before they click
- Aggressively block sites which exhibit too many ‘pairs’ of clicks occurring within short timeframes, n.b. monitoring CVR rates in tandem will go a long way into verifying the safety of a site
- Target smaller geographical areas so that obvious irregularities (location, time, etc) can be identified. E.g. state and city targeting, either by geofence or hard IP list
- Diversify your data analysis. e.g. check your media buyer dashboards for instances where they have registered less impressions and clicks than your MMP
All this is to say: more work is required to limit the impact of click-duplication fraud in an IDFA-less environment. Granular, low-scale, targeted campaigns develop the capacity for anomalies to be more easily identified. As such, we recommended that our advertisers become comfortable with multivariate iOS campaign application in the run up to Q1 2021.
Moving Forward
There is room for interstitial iOS traffic to be a part of any performance advertiser’s plans come January, but we believe a dramatic shift in attitude towards fraud analysis at the network, exchange and MMP levels is required to minimise its risk. At Kaden, we have chosen to turn off some supply relationships for lack of an adequate response to the development of iOS click-fraud in September, and will only turn those partnerships back on when we see tangible developments in their anti-fraud capabilities.
As noted, some MMPs do not apply the same level of anti-fraud rules that Kaden, or indeed other DSPs, do, focusing exclusively on install-level fraud at the expense of click-level and impression-level fraud. Make sure that you are checking for click issues and discrepancies using both your media buying platform partners’ numbers and your MMPs’. Always look for 100% transparency in your partners! Mary Miller @Kochava had this to add about the potential for this type of fraud to become a serious issue for IDFA-less iOS media buying;
“I suspect this fraud will become more prevalent. For two reasons:
- Conversions will have to be probabilistically attributed outside of SKAD network, and the looseness of the logic won’t be getting better (probabilistic attribution now largely relies on the IP the user connected to at ad time and conversion time, and the user agent, of which there aren’t that many in the iOS universe).
- There’s nothing I’ve seen to indicate Apple is attesting to the validity of a ‘click’ in the SKAD network itself – it could be a click (in the classic definition of clicking an ad), or an impression reported as a click, or simply a ‘ping’ from a server. I suspect – as bad as click flooding and stuffing is now – it will be significantly more upon the full rollout of iOS14 +SKAD”
We agree with Mary, and would go as far as to say that the future safety and potential viability of iOS campaigns is in serious doubt. We are working constantly to address fraud in the market, and our Tesera anti-fraud platform is in a continual state of iteration and development as a result. Our video and playable adtech and adserving products put Kaden in an enviable position of being able to minimise this impact of iOS click duplication fraud, but there is a lot of work to do to ensure that we are comfortable exposing our partners to static and animated graphic inventory come January.

 Português
Português 韓國
韓國 日本
日本
